The present-day business world is making big steps in the digital direction. Despite countless benefits, however, this new venue of opportunities also presents up-and-coming companies with an entirely new set of challenges that weren’t so pronounced only a couple of years ago.
These obstacles usually come in the form of cyber security threats that can wreak true havoc upon the companies that are just starting out and still don’t have sufficient infrastructure to fend off countless attacks coming from cyberspace.
It’s always a good idea to hire a professional best rated agency that will take care of your company website design and development. This is very beneficial when it comes to your website security because you will able to get professional help in securing the company website from attacks such as DDOs attacks and so on.
The unique situation in the sense of cyber security threats makes startup security one of the highest priorities of the modern IT sector. Let us take a look then at some of the most common startup security threats your development team should take into consideration when designing the products aimed at this market sector.
1. Phishing

Phishing is a scam strategy where some malicious party tries to trick some of the employees into giving up the info required for accessing the company’s resources.
They are usually sent via email and either request that workers send their sensitive info in the written form for some mock verification process or redirect them to a simulated log-in page they access upon entering their username and password. As simple as these attacks might be, it takes only one distracted worker to make this scheme work.
That is why the developers should put a higher priority on formal communication channels and verification procedures. Phishing can have many different negative effects on businesses.
For example, this can be a way of damaging the business’s reputation, a business can lose money or intellectual property as well. It is also possible for hackers to disrupt operational activities within the company by using this method.
2. Cryptojacking

Essentially, cryptojacking represents a type of malware attack in which the hackers infect the system with embedded scripts commanding the victim’s IT resources to mine cryptocurrency on behalf of the attacker.
As far-fetched as this may seem, cryptojacking is a very serious threat causing more than 15 million security incidents on a monthly basis.
And even though in this case the attackers never try to access the company’s data, the taxing process of mining can make even the most mundane tasks like using Slack slow and tiresome.
And wasting time on simple tasks always causes unforeseen costs and common productivity drops. This is why attacks such as cryptojacking can be even more dangerous for companies than direct money loss since it makes damages that slowly make businesses lose money.
3. Data breach website attacks

Data breaches are some of the simplest and at the same time, the most common and the most dangerous attack the startups can experience.
As their name suggests, they are nothing more than simple brute force attacks on the website and accessing the information that shouldn’t be accessible to the visitors so the best way to deal with them is simply ramping up the website defenses.
This can be accomplished in numerous ways but any company should make getting an SSL certificate one of its top priorities. As for the very technologies, this form of protection is usually achieved through high-level encryption.
4. Ransomware

In its essence, ransomware attacks are very similar to the cryptojacking. In this case, the hackers use the same channels to access some companies’ digital resources. In this case, though, instead of mustering these assets for mining cryptocurrencies, the attackers will simply hold them tied until the companies agree to pay them the extorted ransom.
According to recent surveys, the percentage of global organizations who reported some form of ransomware attacks sits at around 37% which represents a 62% year-on-year increase. The solution to this problem can be found in multiple backups, secure cloud-based servers, and high-level encryption.
5. Focused DDoS attacks
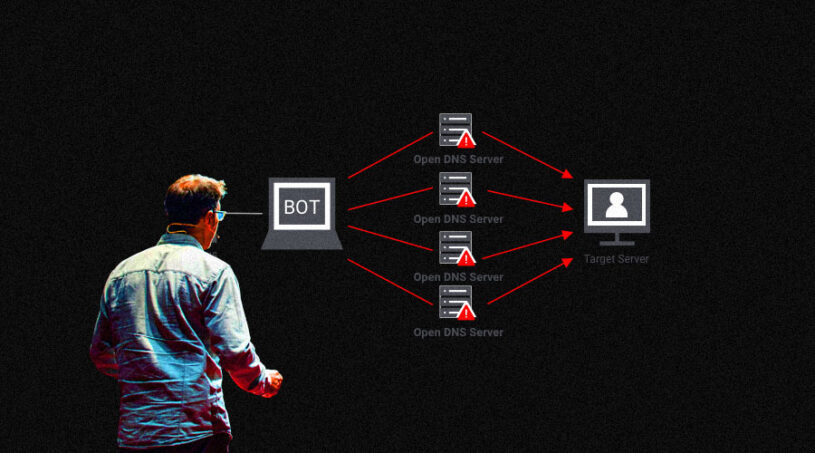
If you are unfamiliar with the term, DDoS stands for distributed denial of service and it represents a form of attack where hackers will overwhelm your servers to the point of crashing and shutting down. This usually happens by funneling requests through multiple connected PCs or IoT devices.
When the servers are overwhelmed into submission the hackers will usually request some sort of ransom to fix this ‘traffic jam’ and allow the attacked party to go back to its daily going. The solution to this common issue is usually found in an added level of protocol verification and more optimized request channel distribution.
6. Employee training

Last but not least, we would like to remind you that, despite countless channels for attacks, the greatest liability in terms of cyber security still comes in the form of people using the system.
No matter how well-designed the defenses might be, the lack of training or knowledge about the cyber security threats will ultimately compromise its overall consistency. That is why the development teams should work very closely with the clients’ companies on keeping the employees up to date with all the security projects that are being implanted as well as provide them basic training about how to keep common attacks at bay and recognize simple threats like poaching.
We hope these few mentions gave you a general idea about where your teams should put their focus when building up the startup’s security systems.
Keeping in mind that the number of organizations entering the business arena grows at an exponential rate it is only expected that the number of attacks aimed at these inexperienced organizations will grow as well.
Finding a solution for all these treats will require a lot of time, patience, and effort but now you know where to start. This simple advantage can considerably relieve your workload.
This is why it’s crucial to take safety measures and adopt protocols in order to protect both websites and users from the possibility of damage and loss.
